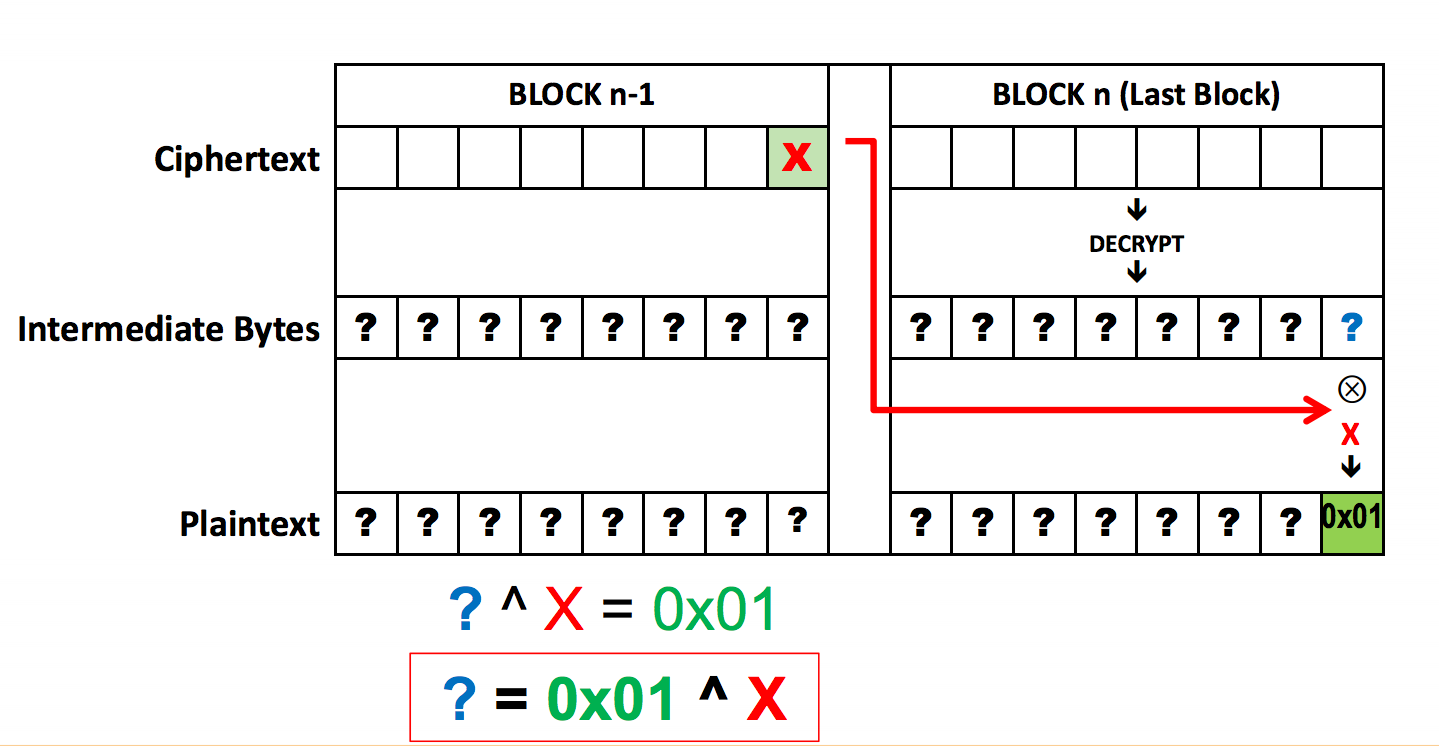
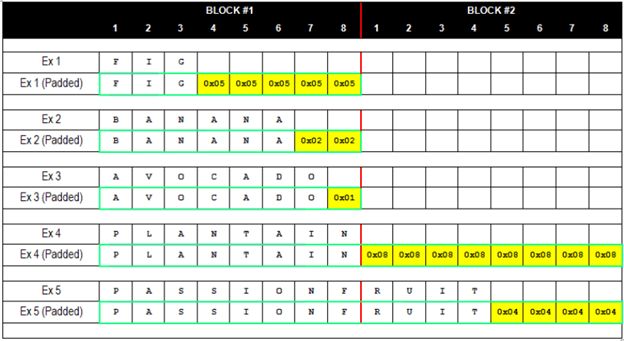
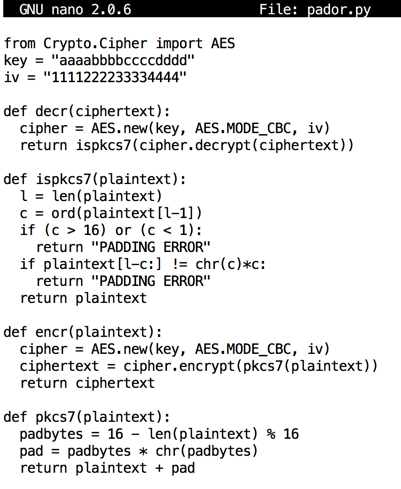
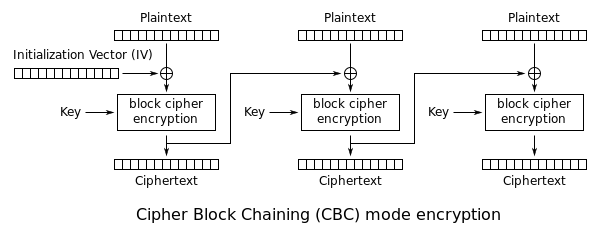
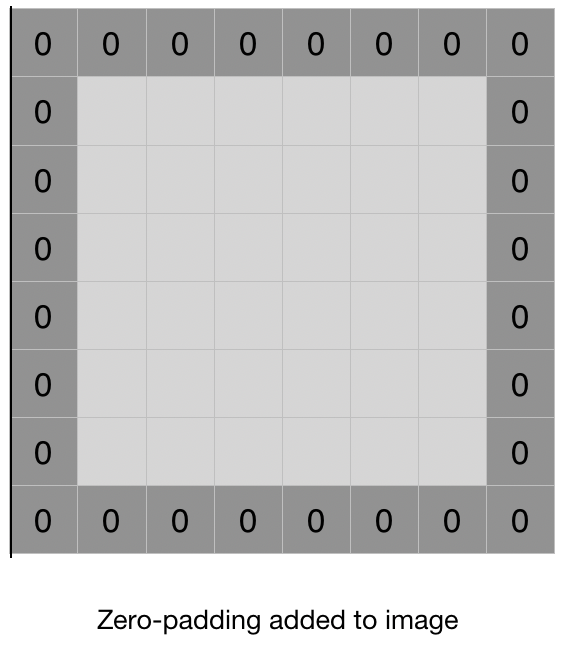
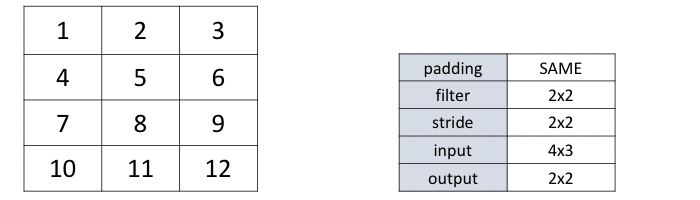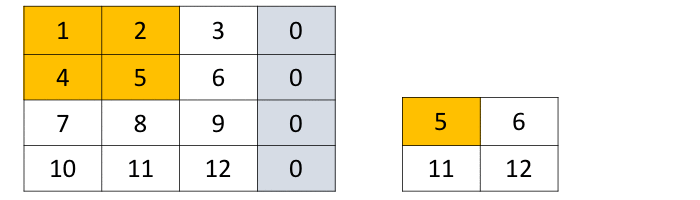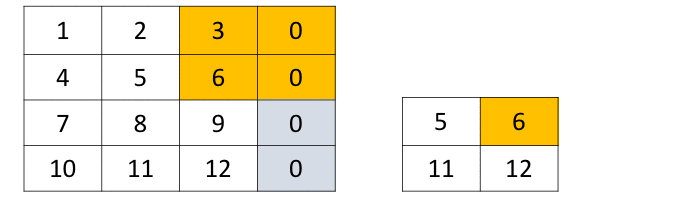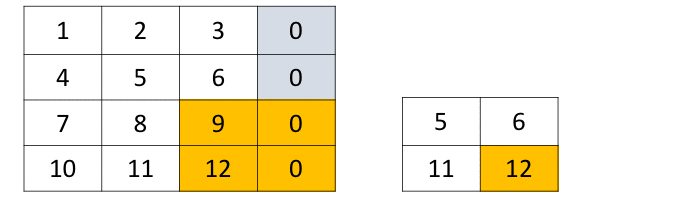
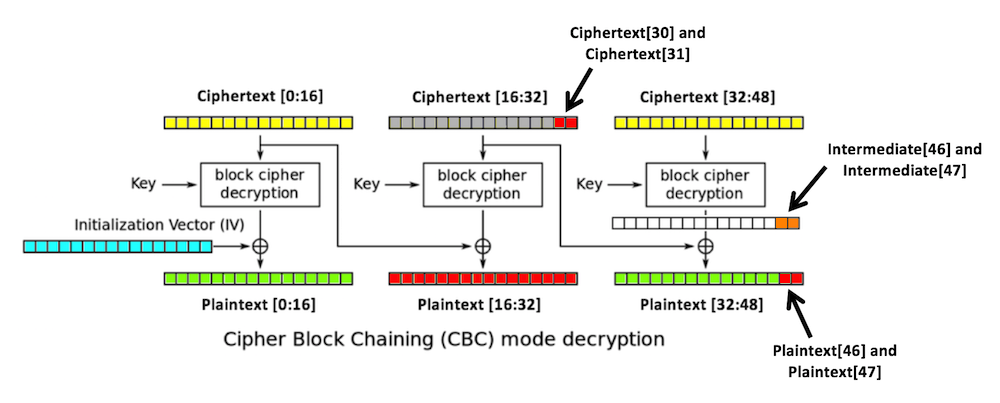
Convolution as a GeMM using the im2col function with 2x2 filter, stride... | Download Scientific Diagram

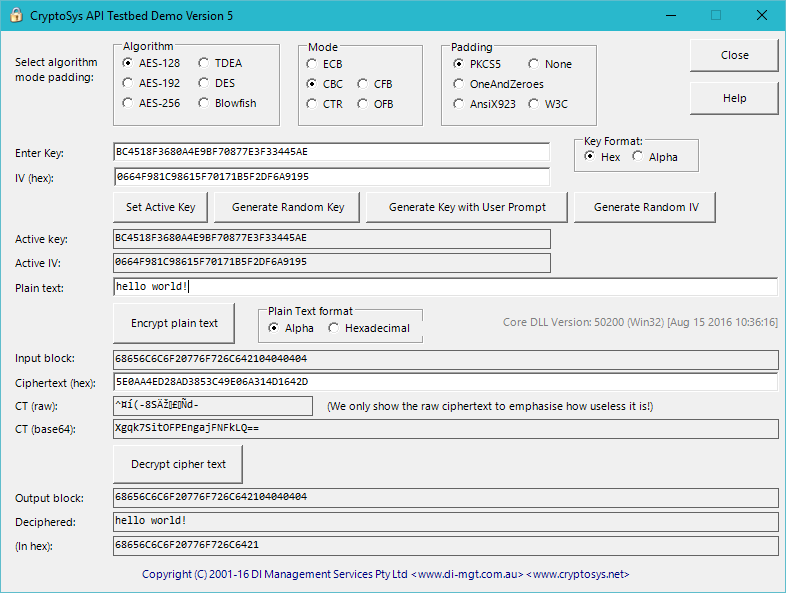
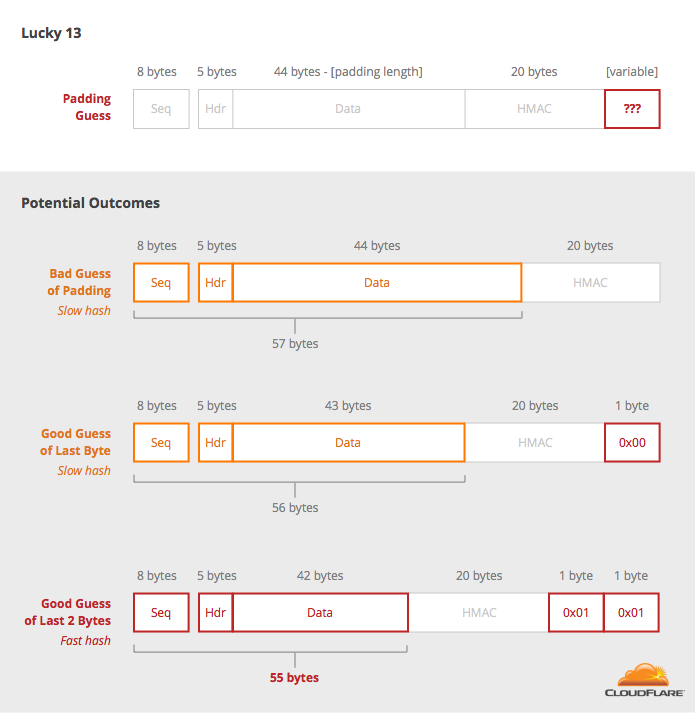
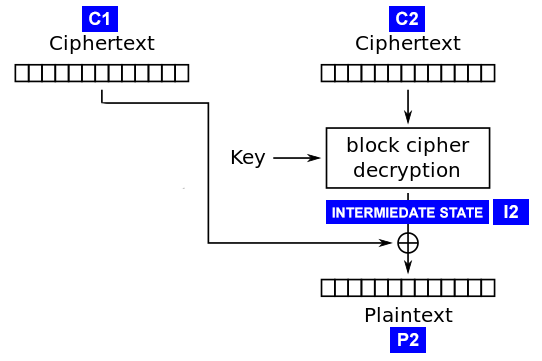
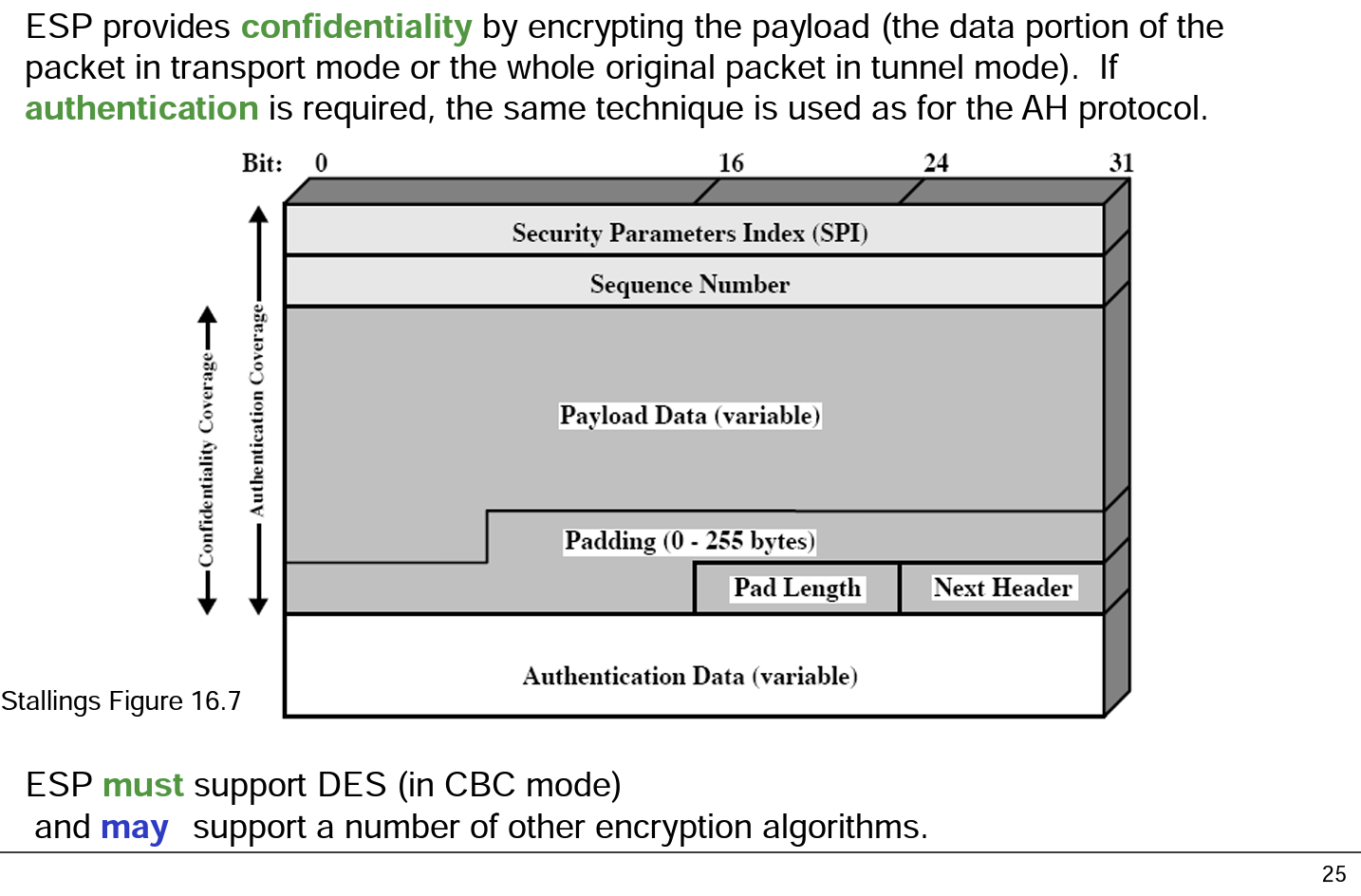
aes - CMAC Generation : If input payload length is not aligned in 16 bytes, what are the possible side effects? - Cryptography Stack Exchange